COVID-19 malicious cyber activity ramps up.

Leading into tax time online scammers are ramping up their criminal activity often impersonating the ATO. This happens year on year, however this year these dodgy scammers are using the spread of COVID-19 to take advantage of people across Australia like never before. Learn what to watch out for & how to spot a scam, but most importantly, be vigilant & NEVER click on an unknown link or respond to an unexpected email / SMS with personal data. If in doubt, DELETE & CALL the provider the message claimed to come from directly.
This information & sample case studies are bought to you by the Australian Cyber Security Centre (ACSC).
Cybercrime actors are pivoting their online criminal methods to take advantage of the COVID-19 pandemic. They are registering COVID-19 themed websites to conduct widespread phishing campaigns that distribute malicious software (malware) or harvest personal information from unsuspecting Australians.
Malicious cyber adversaries will continue to use COVID-19 themed phishing campaigns to obtain user credentials, allowing them to bypass security controls in order to gain access to accounts and networks belonging to individuals and businesses. This could include targeting employees working from home and the remote systems they are relying upon. Sophisticated adversaries will also be focused on covertly obtaining COVID-19 information such as details of Australia’s pandemic responses and research on vaccines and treatments, broadening the types of information they typically target.
Those engaged in cybercrime activities continue to rapidly adapt their techniques in response to changes in the current environment. All organisations and individuals must remain vigilant against the threat of COVID-19 themed cybercrime activity, including sophisticated scams, phishing emails and malicious websites.
The best way to start is to educate yourself and get informed…
COVID-19 themed SMS phishing campaigns
SMS phishing campaigns that seek to trick recipients into clicking on a malicious web link contained in the message are common. While the links appear to come from legitimate organisations, such as the Australian government or a financial institutions, they actually direct the recipient to a malicious website that is hosting malware. For example, in one campaign, the malicious actor is directing people to a website hosting the Cerberus banking Trojan, a form of malware that has been carefully crafted to steal your financial information.
Case study 1: Banking themed SMS phishing campaign
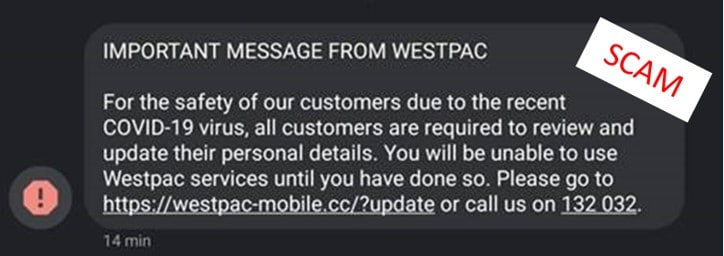
On Monday 30 March 2020, the ACCC received sixteen reports of a Westpac themed phishing text. The link in the SMS directed recipients to a website that attempts to harvest personal information.
COVID-19 payment phishing campaigns using Australian Government branding
There have been a range of payment themed scams targeting Australians that use official Australian Government branding recently. The fraudulent emails come from addresses that very closely resemble or spoof official Australian Government email accounts. The emails aim to trick the recipient into installing malware onto their device and/or to harvest their personally identifiable information (PII).
Case study 2: Phishing campaign pretending to come from Australian Government
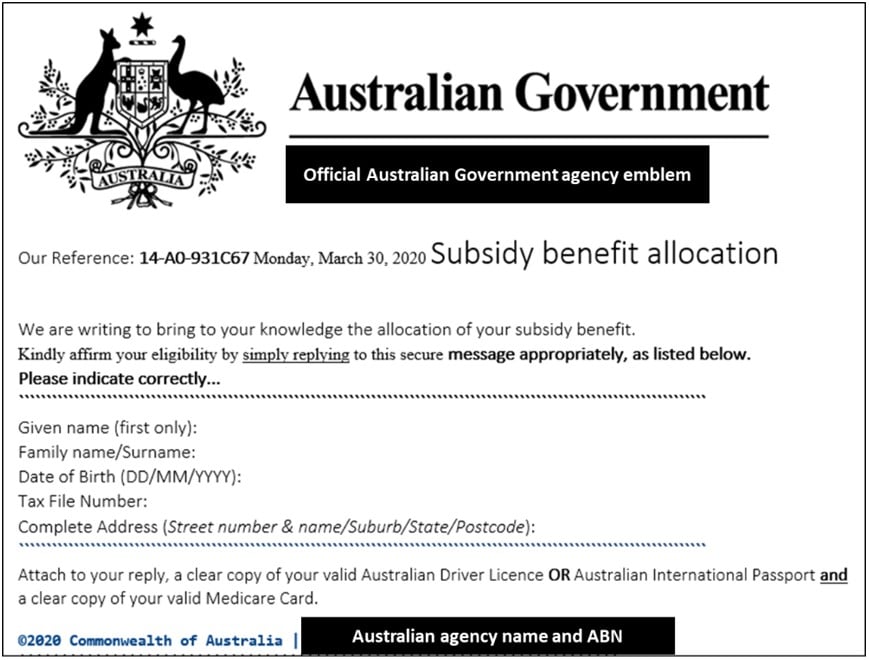
Cybercriminals are also impersonating official Australian Government correspondence about COVID-19 assistance payments in order to steal PII. In this example, the phishing email invites the recipient to provide all of their PII, including tax file number and copies of their identity documents (driver licence or passport and Medicare card) in order to access a benefit payment. Individuals who provide this much personal information are at significant risk of identity theft. With this information, criminals could open bank accounts or take out loans in your name.
Case study 3: Economic stimulus payment phishing email
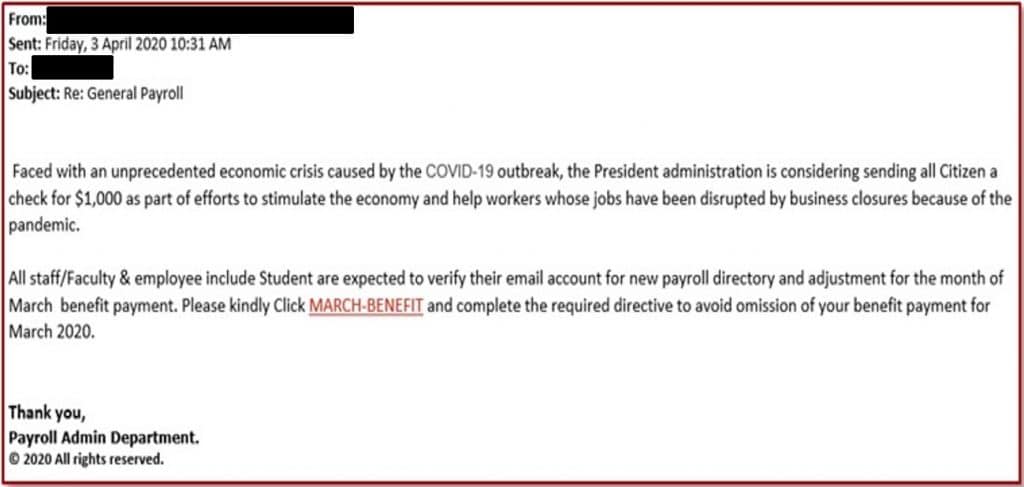
Cybercriminals are preying on people who are out of work and seeking to access financial assistance from the government or their employer. On 3 April 2020, this phishing email was sent to hundreds of employees within a large Australian company. Recipients were asked to click on the link in order to receive a $1,000 benefit payment to be delivered in the March payroll. The link re-directs users to a website designed to install malicious software onto the company’s corporate network.
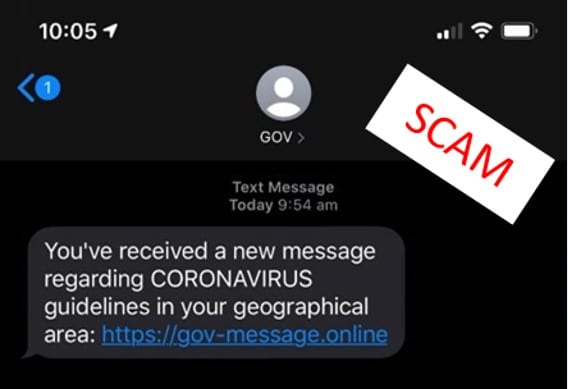
SMS phishing scams about COVID-19 testing and restrictions
Malicious emails and text messages from cybercriminals that claim to provide information on how to get tested for, or stay protected from, COVID-19 have surfaced. These malicious messages claim to be from Australian Government agencies or other trusted sources such as the World Health Organisation (WHO). They try to convince the recipient to click on a link or open an attachment that will then install malware and steal sensitive information such as bank account details.
Case study 4: COVID-19 testing themed SMS phishing campaign
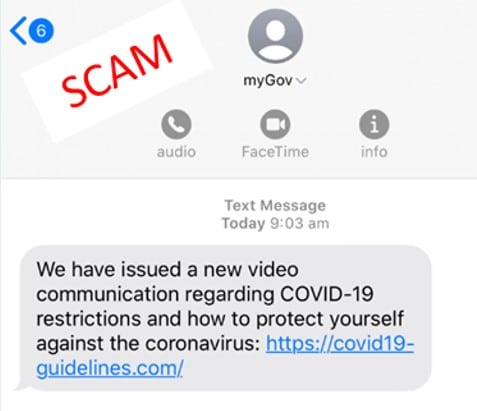
Remote access scams targeting people working from home
The ACSC has also been receiving an increasing number of reports from businesses and members of the public about remote access scams. Most of these reports indicate that the scammers are pretending to be from IT companies, telecommunications companies, banks, and even from the ACSC. Cybercriminals often attempt to persuade you to give them remote access to ‘fix an issue’ and will provide a range of scenarios to convince you that they need immediate access to your device.
Allowing anyone access to your devices can, and usually does, result in devastating consequences, including financial loss or the compromise of your personal accounts. If you are unsure about the identity of a caller, just hang up and check their official website for the legitimate contact details and then call them back.
Fraudulent payments over the internet and business email compromise
Cybercriminals continue to adapt previously successful methodologies to leverage the COVID-19 pandemic, and one such approach is known as business email compromise, or fraudulent payments over the internet. This method attempts to convince businesses and/or clients to redirect payments, such as payroll or supplier and invoice payments, to a bank account run by the criminals. Cybercriminals attempting to obtain fraudulent payments over the internet will often use a compromised email account, or a spoofed/fake email address of the business, supplier, or client. Scams like this commonly target businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments.
Mitigation strategies for combatting COVID-19 scams and phishing emails
How to spot if an email or text message is phishing
There are some key details to look out for to help determine if a text message or email is phishing:
- Read the message very carefully, look for anything that isn’t quite right, such as spelling, tracking numbers, names, attachment names, sender, message subject and URLs.
- On a PC or laptop, hover your mouse over links to see if the embedded URL is legitimate, but don’t click.
- Google information such as sender address or subject line, to see if others have reported it as malicious.
- Call the organisation on their official number as it appears on their website (separate to any contact details in the received message) and double-check the details or confirm the request is legitimate. Do not contact the phone number or email address contained in the message, as this most likely belongs to the scammer.
- Use sources such as the organisation’s mobile phone app, web site or social media page to verify the message.
Protect yourself against phishing emails
As shown in the examples above, cybercriminals and scammers produce phishing emails that look legitimate. By following these simple steps, you can assist in protecting yourself against phishing emails:
- Before opening an email, consider who is sending it to you and what they’re asking you to do. If you are unsure, call the organisation you suspect the suspicious message is from, using contact details from a verified website or other trusted source.
- Do not open attachments or click on links in unsolicited emails or messages.
- Do not provide personal information to unverified sources and never provide remote access to your computer.
- Remember that reputable organisations locally and overseas, including banks, government departments, Amazon, PayPal, Google, Apple and Facebook, will not call or email to verify or update your personal information.
- Use email, SMS or social media providers that offer spam and message scanning.
- Use two-factor authentication (2FA) on all essential services such as email, bank and social media accounts, as this way of ‘double-checking’ identity is stronger than a simple password. 2FA requires you to provide two things, your password and something else (e.g. a code sent to your mobile device or your fingerprint) before you, or anyone pretending to be you, can access your account.
The ACSC has published a range of information about COVID-19 related malicious activity, as well as guidance on securing remote working and video conferencing. For more information, please visit:
Cyber security is essential when preparing for COVID-19
Threat update: COVID-19 malicious cyber activity, 27 March 2020
COVID-19 scam messages targeting Australians
Protecting small business against cyber attacks during COVID-19
COVID-19: Cyber security tips when working from home
Source: Australian Cyber Security Centre https://www.cyber.gov.au/threats